A hacker has posted a list of one-line exploits to steal VPN credentials from almost 50,000 Fortinet VPN devices.
Present on the list of vulnerable targets are domains belonging to high street banks and government organizations from around the world.
Researchers find thousands of targets
The vulnerability being referred to here is CVE-2018-13379, a path traversal flaw impacting a large number of unpatched Fortinet FortiOS SSL VPN devices.
By exploiting this vulnerability, unauthenticated remote attackers can access system files via specially crafted HTTP requests.
The exploit posted by the hacker lets attackers access the sslvpn_websession files from Fortinet VPNs to steal login credentials. These stolen credentials could then be used to compromise a network and deploy ransomware.
Although the 2018 bug was publicly disclosed over a year ago, researchers have spotted around 50,000 targets that can still be targeted by attackers.
This week, threat intelligence analyst Bank_Security found a hacker forum thread where a threat actor shared a large 49,577 device list of such exploitable targets.
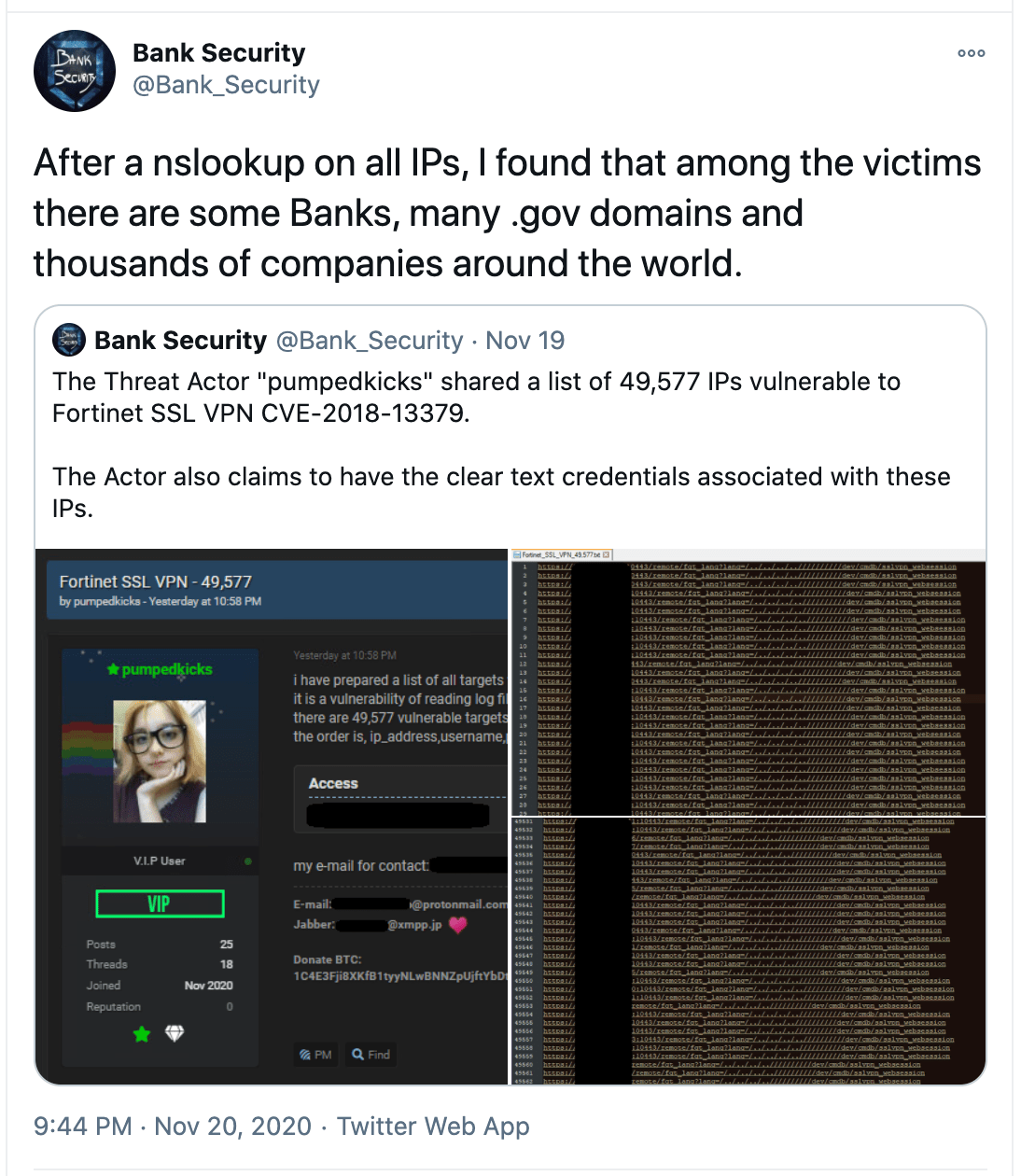
After analyzing the list, it was found that the vulnerable targets included government domains from around the world, and those belonging to well-known banks and finance companies.
Banks, finance, and govt organizations vulnerable
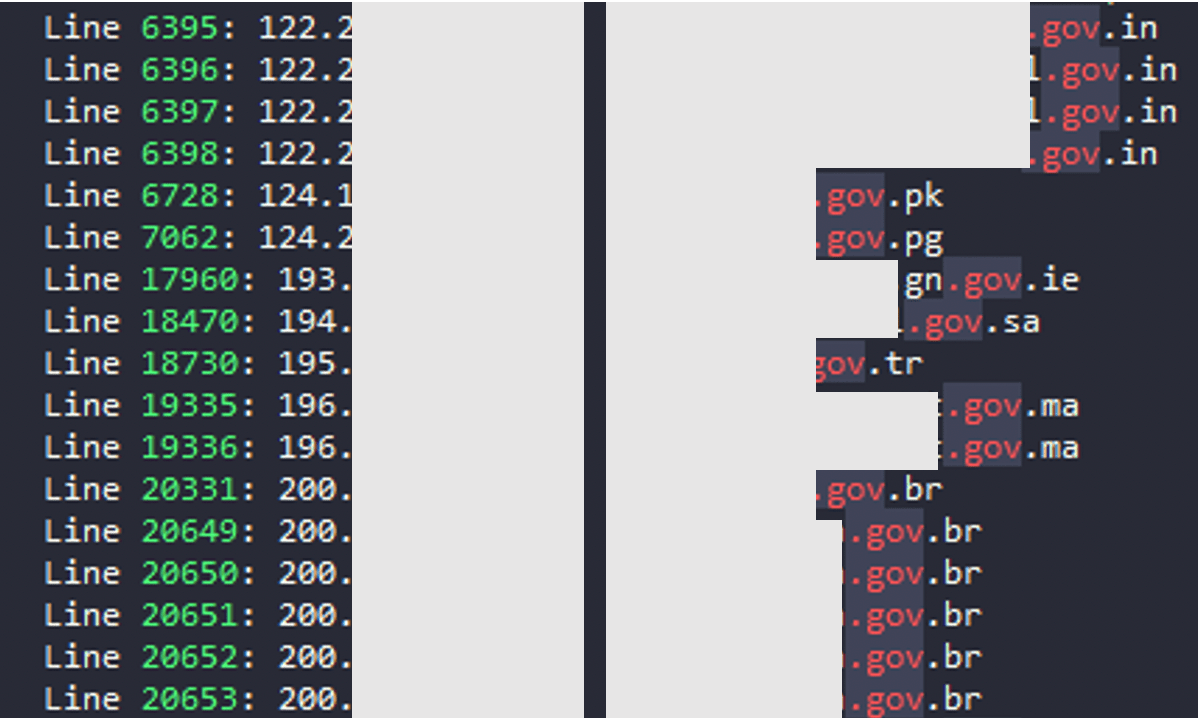
As observed by BleepingComputer, out of the 50,000 domains, over four dozen belonged to reputable banking, finance, and governmental organizations.
Bank Security told BleepingComputer after he saw the forum post, he started analyzing the list of IPs to identify what all organizations were impacted.
"To better find out which companies were impacted, I launched an nslookup on all the IPs on the list and for many of them, I found the associated domain."
The analyst then refined the obtained results to identify domain names associated with organizations of interest and notable banks.
The analyst further told BleepingComputer, although this is an old bug that is trivial to exploit, organizations have "a very slow" patching process, enabling attackers to continue exploiting well-known bugs:
"This is an old, well known and easily exploited vulnerability. Attackers already use it for a long time. Unfortunately, companies have a very slow patching process or an uncontrolled perimeter of exposure on the internet, and for this reason, attackers are able to exploit these flaws to compromise companies in all sectors with relative simplicity."
As reported by BleepingComputer last month, the same flaw was leveraged by attackers to break into US government elections support systems.
Network administrators and security professionals are therefore encouraged to patch this severe vulnerability immediately.
Update, 23-Nov-2020:
Fortinet has issued a statement with regards to this vulnerability:
"The security of our customers is our first priority. In May 2019 Fortinet issued a PSIRT advisory regarding an SSL vulnerability that was resolved, and have also communicated directly with customers and again via corporate blog posts in August 2019 and July 2020 strongly recommending an upgrade," a Fortinet spokesperson told BleepingComputer.
"In the last week, we have communicated with all customers notifying them again of the vulnerability and steps to mitigate. While we cannot confirm that the attack vectors for this group took place via this vulnerability, we continue to urge customers to implement the upgrade and mitigations. To get more information, please visit our updated blog and immediately refer to the May 2019 [PSIRT] advisory," concluded Fortinet.


